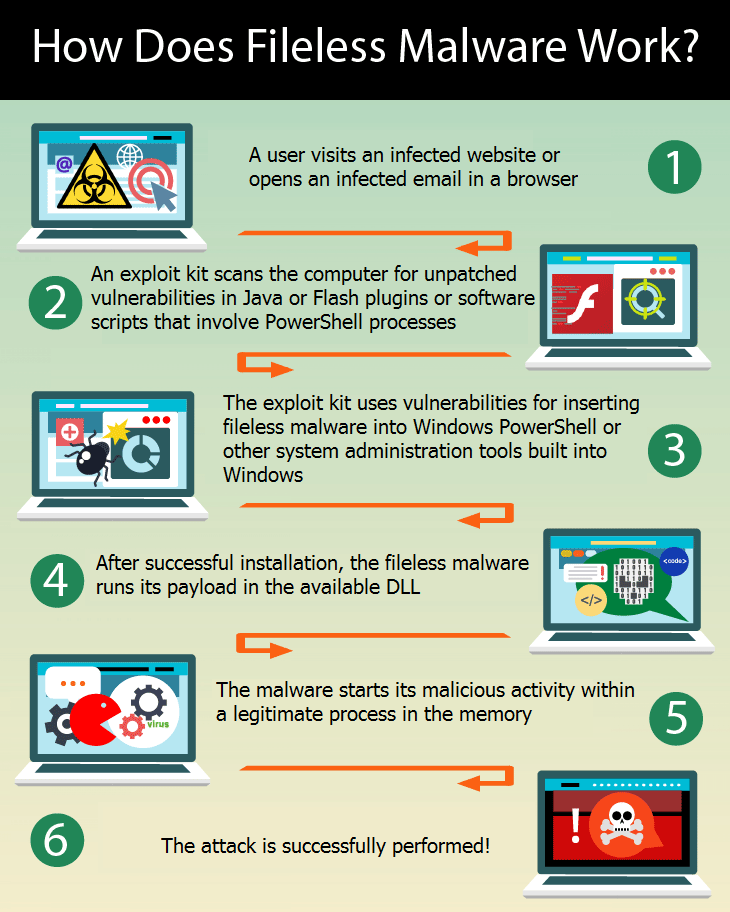
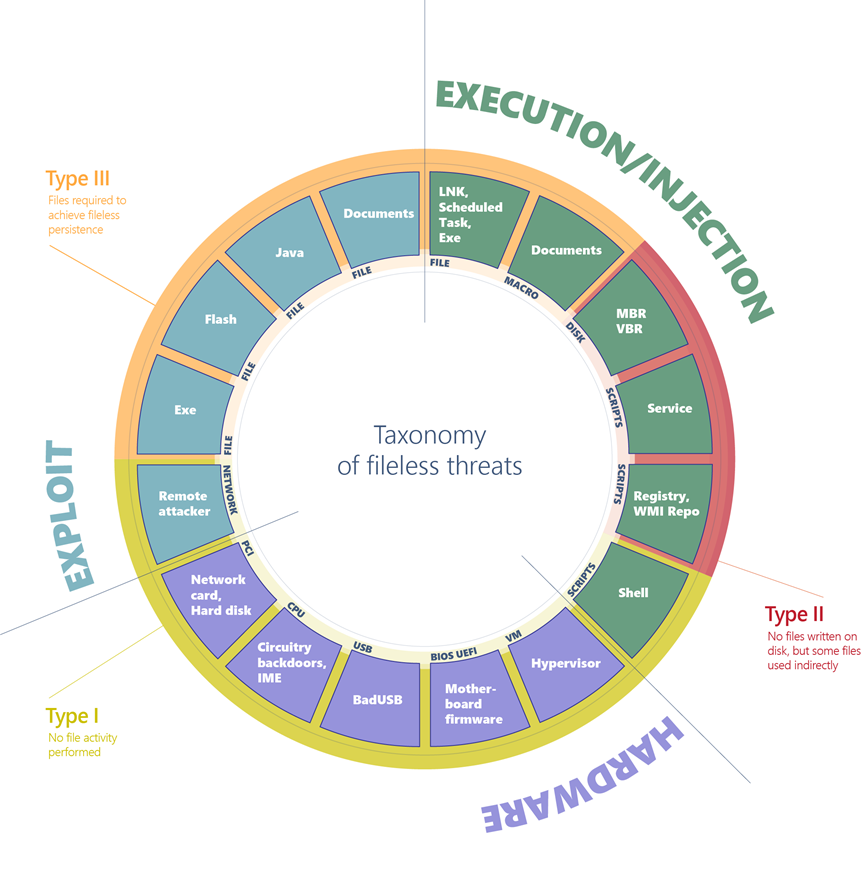
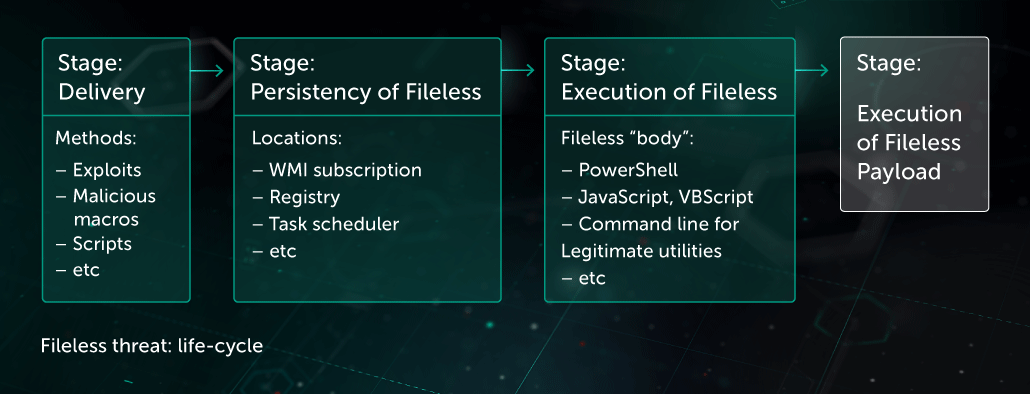
Product Name: Fileless malware hotsell
What Is Fileless Malware Trellix hotsell, What is Fileless Malware . What Is a Fileless Attack by Nelson hotsell, What is a fileless attack How hackers invade systems without hotsell, Fileless malware mitigation Sysdig hotsell, Living off the Land Fileless Malware infoaxis hotsell, The Art of Fileless Malware hotsell, What is Fileless Malware PowerShell Exploited hotsell, Fileless Cryptocurrency Mining Malware Uses New Technique hotsell, What is Fileless Malware EasyDMARC hotsell, What Are Fileless Malware Attacks Pratum hotsell, What is Fileless Malware PowerShell Exploited hotsell, Fileless Malware Executing in Containers Aqua hotsell, Stopping Fileless Malware Behavioral Analytics and Machine hotsell, Fileless Malware What It Is and How It Works Fortinet Blog hotsell, Fileless Malware Detection A Crash Course hotsell, The anatomy of a completely fileless attack Help Net Security hotsell, Fileless Malware hotsell, What is fileless malware NordVPN hotsell, Fileless Malware The Rise of a New Threat Ophtek hotsell, Fileless Malware Specifics Detection and Protection Tips Apriorit hotsell, Fileless Malware The What How hotsell, Fileless threats Microsoft Learn hotsell, Fileless Threats Protection Kaspersky hotsell, How Fileless Ransomware Works Infographic CrowdStrike hotsell, Intro to Fileless Malware in Containers hotsell, Fileless Malware Poses New Threat to Computer Users Brady Martz hotsell, Experts warn against uptick in fileless malware attacks The hotsell, What are Fileless Malware Attacks Deep Instinct hotsell, What Is Fileless Malware hotsell, How to remove fileless malware hotsell, Risks Under the Radar Understanding Fileless Threats Security hotsell, What is Fileless Malware PowerShell Exploited hotsell, What is Fileless Malware Attack Understanding hotsell, Sensors Free Full Text An Insight into the Machine Learning hotsell, Review Fileless Malware Definition Detection Affect Removal hotsell.
Fileless malware hotsell